Creating malware visualizations with Ghidra and CantorDust
 |
|---|
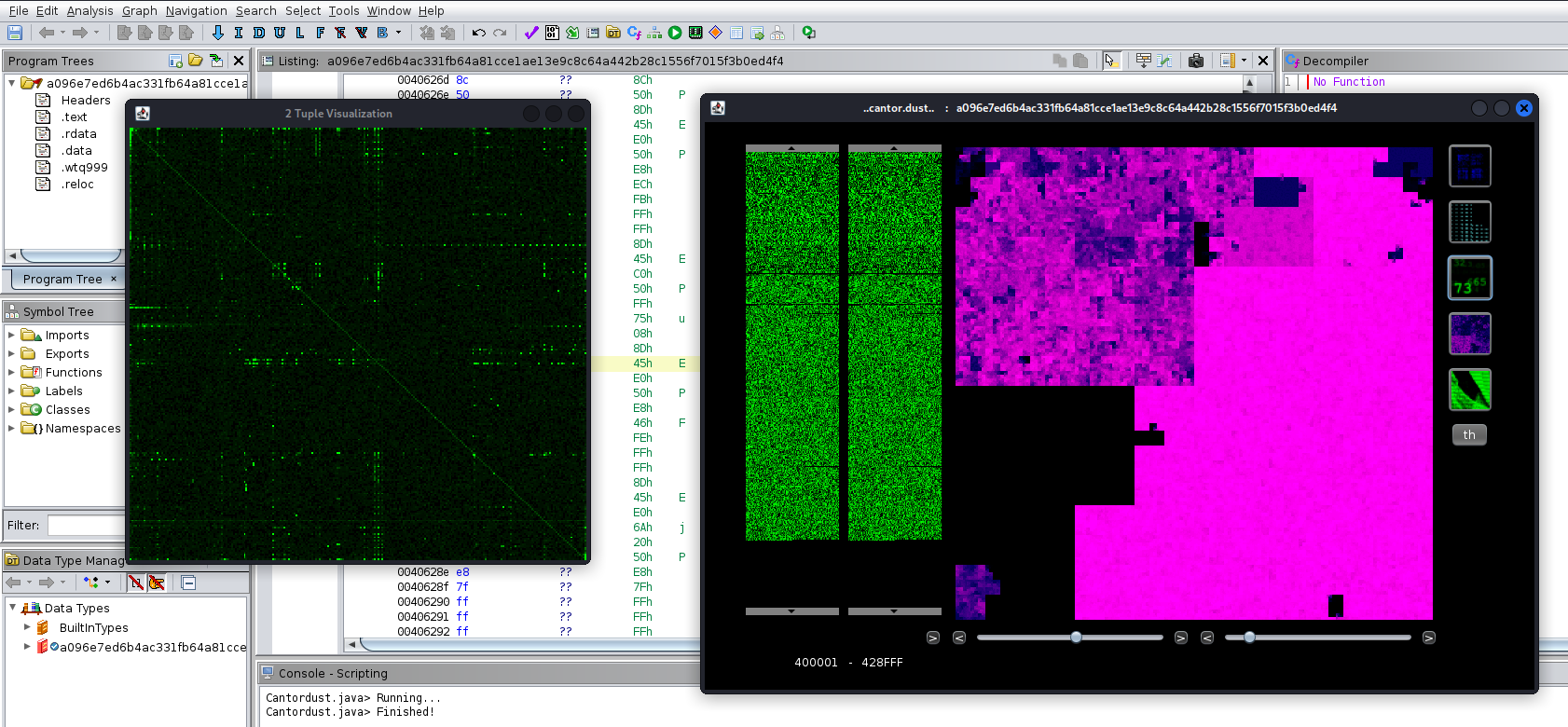
| Cantordust Ghidra plugin - Visualization of REvil ransomware sample |
..cantor.dust.. is a binary visualization tool developed by Christopher Domas, first presented at Derbycon 2012. The original source code was never released. Then in 2020 a plugin for Ghidra was released by Battelle - (https://github.com/Battelle/cantordust)
Visualizing binaries in this way could assist forensics and reverse-engineering teams in the initial triage and categorization of unknown files. Battelle shared on their blog why they think this is important and details about how the visualizations work - (https://inside.battelle.org/blog-details/battelle-publishes-open-source-binary-visualization-tool)
Installation
I’ve had the cantordust plugin running successfully on both Windows and Linux based installations of Ghidra.
The instructions provided by Battelle are enough to get started - (https://github.com/Battelle/cantordust#installation-and-setup)
Examples
Here are some malware visualizations I’ve generated using samples from both theZoo and vx-underground
 |
 |
|---|---|
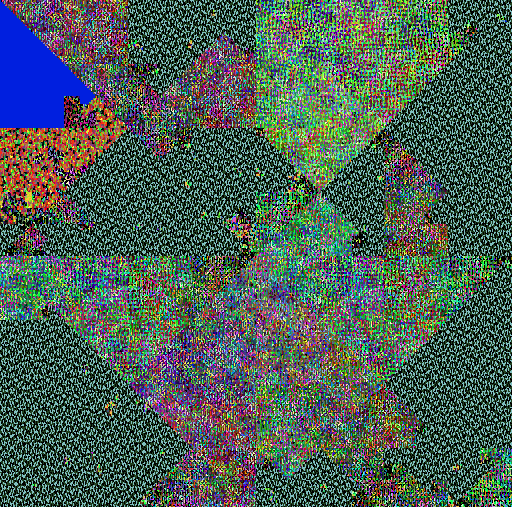
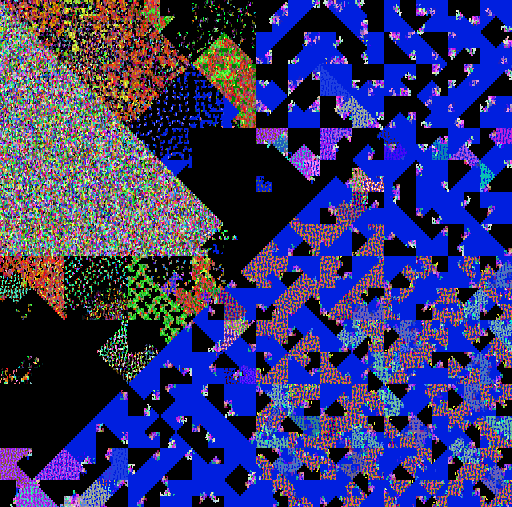
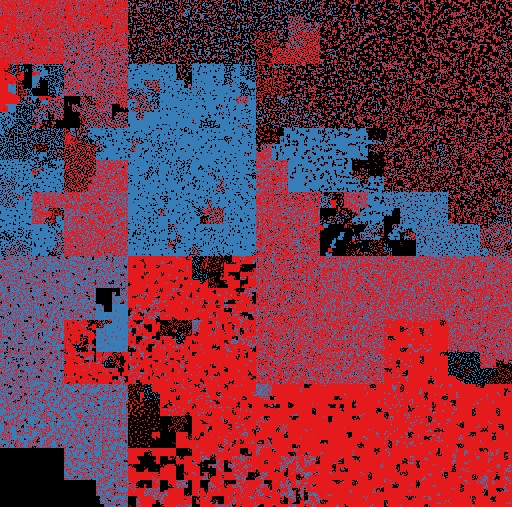
| AlienSpy | CobaltStrike |
 |
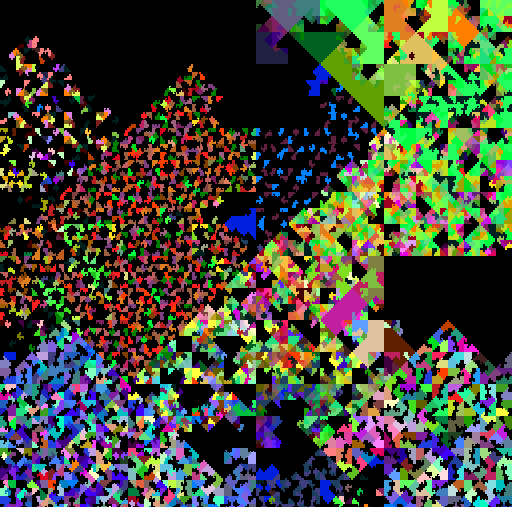 |
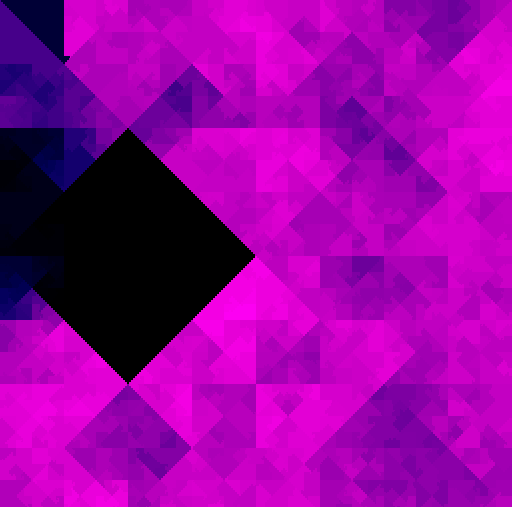
| Darkside | Emotet |
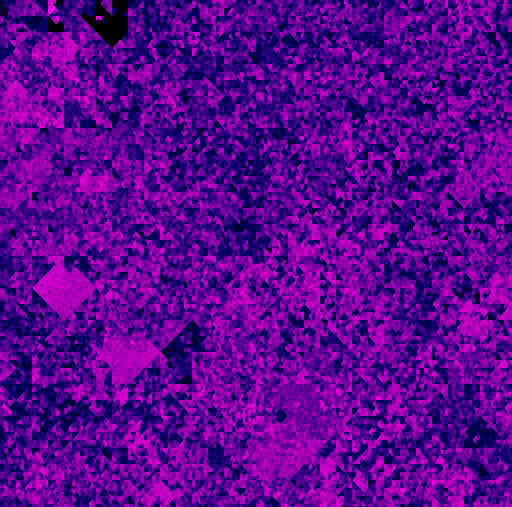 |
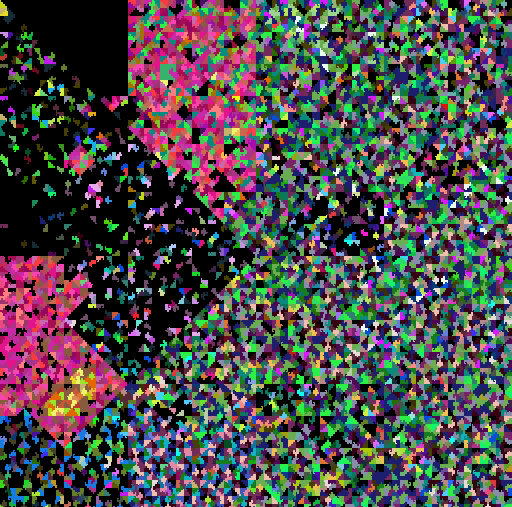 |
| Mirai | Pegasus |
 |
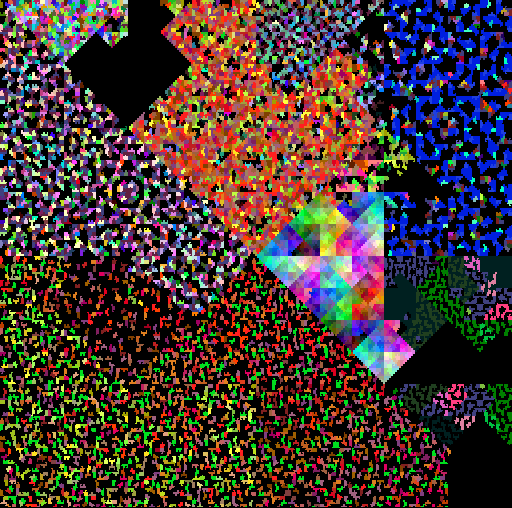 |
| Petya | REvil |
 |
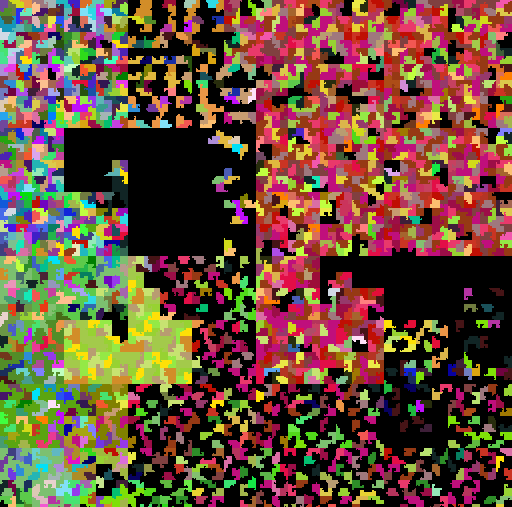 |
| Shadow Hammer | Stuxnet |
Similar Projects
- https://rustrepo.com/repo/sharkdp-binocle-rust-data-visualization
- https://github.com/wapiflapi/veles
- https://github.com/VelocityRa/binviz
References
- https://sites.google.com/site/xxcantorxdustxx
- https://github.com/Battelle/cantordust
- https://inside.battelle.org/blog-details/battelle-publishes-open-source-binary-visualization-tool
- https://www.youtube.com/watch?v=4bM3Gut1hIk
- https://bdtechtalks.com/2021/09/10/computer-vision-deep-learning-threat-detection